Behavioral Signals’ AI-MC software solution can be installed in a fully protected and isolated network zone on the organization’s premises since it does not require any connection to the internet. We, also, offer deployment on the cloud, based on the most secure global cloud infrastructures (Microsoft Azure or Amazon Web Services). We use industry standards for encryption, multi-factor authentication, VPNs, backup, data restoration, and prevention of attacks. Our company is GDPR and CCPA compliant, in respect to user & data privacy, and certified for secure handling of said data via the SOC 2 standards protocol.
AI-MC by Behavioral Signals is effectively matching each of your customers with the right agent at the call center. It can significantly improve agent-customer communication and lead to an increase in call-success ratio, measured in terms of promises-to-pay achieved, debt restructuring applications made, customer satisfaction, or a similar KPI. To evaluate the AI-MC solution and quickly assess the added value it brings to your business without disrupting your day-to-day operations you can use the Behavioral Signals’ AI-MC POV-Lite engine.
Initialization
– Call recordings from 3 months in the past (or 50K calls, minimum) available in a network shared folder or transferred (sftp/scp/ftp/http) to the POV-Lite engine
– 8kHz, single or two-channel recordings are supported; wav/mp3/vox/gsm audio formats are supported
– Corresponding metadata in the form of csv/json/xml files
Simulation
Simulation typically runs on a separate dataset, comprising the same metadata but for a different time period. The system generates a report of all relevant analytics.
Functional Specifications
The POV-Lite engine becomes available as a VM image no bigger than 30GB that can be installed on an on-premises hypervisor (e.g., vCenter, VirtualBox, Hyper-V). A download link is typically provided. The VM is built with the following configuration: 16vCPUs, 32GB of RAM, 500GB storage (SSD)
The system provides a graphical user interface to allow users to:
— Configure engine training, upload metadata, and monitor engine status
— Review basic training dataset analytics (i.e., number of portfolios, number of agents, number of calls, date range, call durations)
— Upload simulation metadata, run the simulation, and get simulation results
SECURITY SPECIFICATIONS
Infrastructure
The engine is installed as a Virtual Machine (VM) on the hypervisor. The Operating System of the VM is Ubuntu Linux 18.04 and the engine technology stack comprises the following:
— An Application Programming Interface (API) written in java and python and providing full access to basic engine functionality
— A python service (POV-Lite backend) to handle incoming audio and metadata and connect to data sources specified by the user
— A rethinkDB database where incoming metadata are stored
— Separate microservices for behavioral profile estimation, profile pairing, and behavioral grouping
— A message broker based on ActiveMQ to allow asynchronous batch processing of audio data
— Microservices written in python and C++ to perform operations such as: speaker diarization (identify who speaks when in the audio), feature extraction, behavioral profile estimation, model training, automatic call distribution simulation
— The graphical user interface (GUI) implemented as a web application in javascript (using React and partly also the Dash platform) that allows: a) engine administration, b) reviewing training data analytics, c) running the simulation.
— All services are deployed as docker containers in the VM and full logging is provided using Elasticsearch, Logstash, and Kibana.
Network Architecture
AI-MC can be installed in a fully protected and isolated network zone on the organization’s premises since it does not require any connection to the internet. The network architecture recommended for the deployment of the POV-Lite engine is shown in the following diagram:
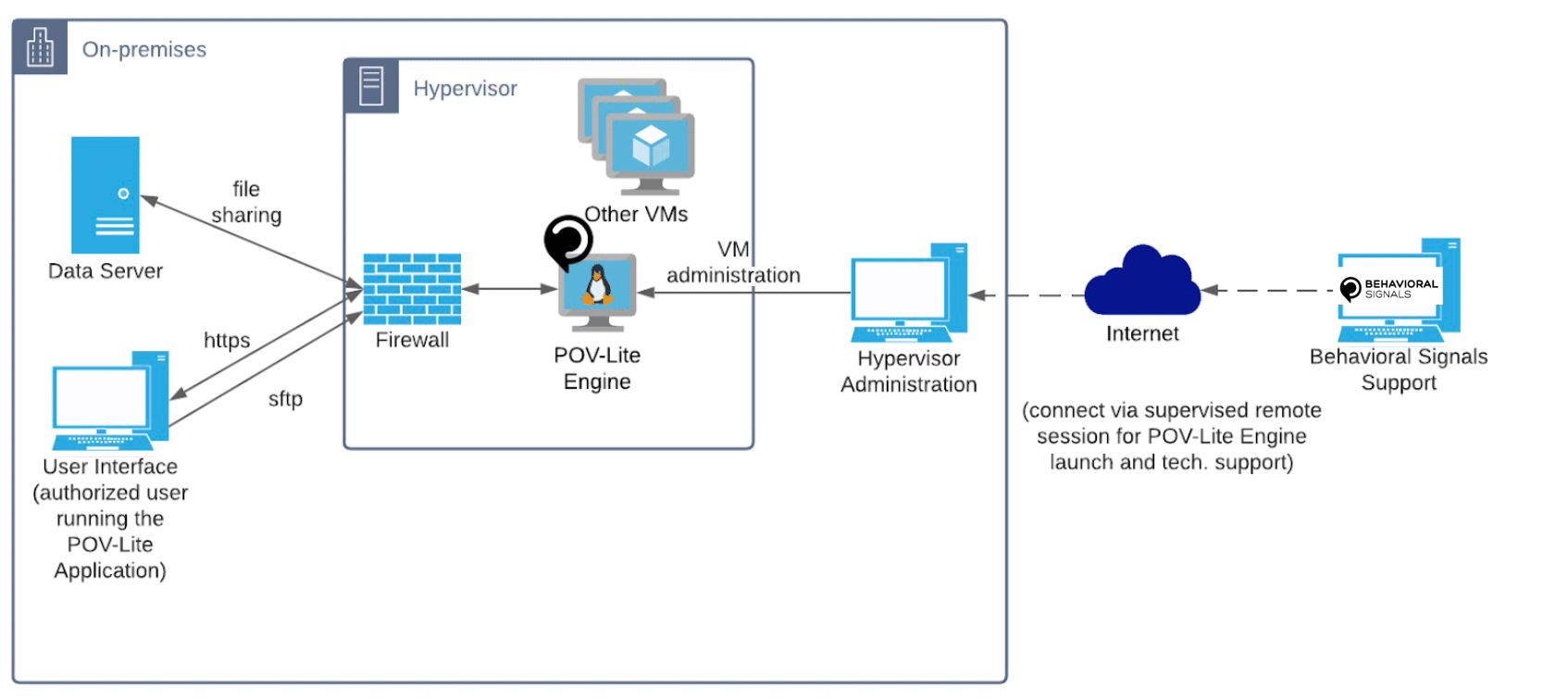
It is important to note that the POV-Lite engine does not initiate any outbound traffic in the network. Outbound traffic is generated only in response to specific user requests, e.g., when the user is using the GUI and wants to see the results of the simulation, and only towards the network client that made the request. An internal firewall (using ufw) is activated to control inbound or outbound traffic (denying traffic on all unnecessary ports). An external firewall, fully controlled by the user (i.e., the organization that has installed the engine), can, of course, also be applied at the hypervisor level as an extra security control in case that is required due to stricter security specifications.
Data Security
The POV-Lite Engine is fully encrypted to protect it from malicious software injection as well as to protect intellectual property. Further, services inside the virtual machine run with the minimum required ownership and permissions.
More specific information regarding data security is provided in the following:
Data at Rest:
– Sensitive data in databases is protected by column level encryption
– Files created temporarily during processing are deleted once they are not needed anymore.
Data at transfer:
Internal Data Transfer
> TLS is being used to encrypt communications between microservices with sensitive data within the POV-Lite engine.
External Data Transfer
> TLS to encrypt the communication between services exposed to the outside world.
— https is used between the AI-MC UI and the AI-MC master service to exchange audio metadata and configurations.
> Supported audio transfers from the external world to the VM:
— sftp to transfer audio files within the VM manually
— SMBv3.1.1 with password authentication to get audio files from a shared network folder automatically.
Authorization-Authentication-Auditing
The POV-Lite engine VM image is built and tested by an automated CI/CD process (using Jenkins) which is managed only by authorized personnel at Behavioral Signals. Distribution of the POV-Lite engine to external partners or customers and technical support is done only after authorization from Behavioral Signals management and only by authorized Behavioral Signals personnel. Credentials to decrypt and login to the POV-Lite engine VM are only shared by authorized Behavioral Signals personnel.
Regarding authentication:
– Password level authentication is required to decrypt the VM and start it (that is only available to the Behavioral Signals support team and is typed in during a tech-support remote session with the customer’s IT team).
– Password level authentication is required to login into the VM for technical support purposes (that is only available to the Behavioral Signals support team)
– Password level authentication is required for transferring data to the VM (the password is available to authorized customer’s personnel)
– Password level authentication is required for using the POV-Lite web application for configuration and management of the POV-Lite engine (the password is available to authorized customer’s personnel).
Auditing:
– All POV-Lite processes are logged and corresponding information is available to the user via a separate https interface. These logs clearly show the entire data lifecycle inside the POV-Lite engine.
Technology Modules
Docker Engine
RethinkDB
Python
Java
Kaldi
ActiveMQ
Adminer
Node.js
Dash



Our technical team is always available to provide further information on all our technical processes. Ask us today how we can work together while fully protecting your data.

